The attackers who stole $81 million (£55.8 million) from the Bangladesh central bank probably hacked into software from the SWIFT financThe 2016 Bangladesh Bank heist is a notable example of a sophisticated cyber attack on the SWIFT network. Here's a step-by-step breakdown of the key technical aspects of the attack
In the cyber-security industry the North Korean hackers are known as the Lazarus Group, a reference to a biblical figure who came back from the dead; experts who tackled the group's computer viruses found they were equally resilient.
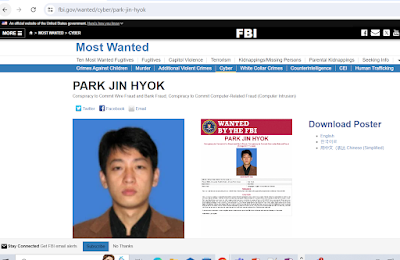
Little is known about the group, though the FBI has painted a detailed portrait of one suspect: Park Jin-hyok, who also has gone by the names Pak Jin-hek and Park Kwang-jin.
1. Initial Compromise
Phishing Attack:
- The attackers initially compromised the Bangladesh Bank's system by sending spear-phishing emails to employees.
- These emails contained malicious attachments, which, when opened, installed malware on the bank's network.
2. Gaining Access
Malware Deployment:
- The attackers deployed custom malware designed to gain access to the bank’s internal network and the SWIFT system.
- The malware allowed the attackers to monitor the network and obtain credentials and other necessary information.
3. Understanding the Network
Reconnaissance:
- After gaining access, the attackers spent several months conducting reconnaissance.
- They learned how the bank’s SWIFT system operated, identified key personnel, and understood the network topology.
4. Manipulating the SWIFT Software
Modifying SWIFT Software:
- The attackers altered the bank’s SWIFT Alliance Access software.
- They inserted malware that intercepted and manipulated legitimate SWIFT messages.
- This malware also deleted the fraudulent transaction logs to cover their tracks.
5. Initiating Fraudulent Transactions
Sending Unauthorized Transactions:
- The attackers used the SWIFT credentials they had stolen to send fraudulent messages.
- They sent about 35 fraudulent SWIFT transfer requests, totaling nearly $1 billion, from the Federal Reserve Bank of New York to accounts in the Philippines and Sri Lanka.
6. Avoiding Detection
Evasion Tactics:
- The malware prevented the bank from receiving confirmation messages about the transactions.
- It altered the transaction records to hide evidence of the fraudulent transactions.
7. Laundering the Money
Money Laundering:
- Once the money reached the recipient accounts, it was quickly moved through a series of transactions to launder it.
- In the Philippines, some of the funds were laundered through casinos, making it difficult to trace.
Detection and Response
Discovery:
- The fraudulent transactions were eventually discovered when a typo in one of the transfer requests (spelling “foundation” as “fandation”) triggered suspicion and led to a manual review.
- The Federal Reserve Bank of New York contacted Bangladesh Bank to verify the suspicious transactions.
Investigation:
- Upon discovering the breach, Bangladesh Bank and international authorities began an investigation.
- It was found that about $81 million had been successfully stolen.
Key Takeaways
Security Measures:
- Regular updates and patches to systems to protect against vulnerabilities.
- Enhanced monitoring and anomaly detection systems to identify suspicious activities.
- Multi-factor authentication for accessing critical systems and networks.
- Employee training to recognize and respond to phishing attempts.
The Bangladesh Bank heist underscored the need for robust cybersecurity measures and the risks associated with sophisticated cyber attacks on financial institutions.ial platform that is at the heart of the global financial system, said security researchers at British defence contractor BAE Systems.
- Anonymous.
- Fancy Bear, APT29 (Cozy Bear), and Pawn Storm.
- Lazarus Group.
- Carbanak (Anunak).
- The Dark Overlord.
- The Equation Group.
- TA505 (Evil Corp) .
- DarkSide.

Comments
Post a Comment